Tuesday, 4 September 2012
Online Shopping and Security Tips
Online shopping now is very popular in this era. Many people use online way to shop rather than go to real shop. This point is cause of reduce time and energy. But many people don't know the risk of shopping online. Many way of hacker could steal our data from online shopping transaction.
In this video there are some tips to avoid some of hacking or tracking action in online shopping activity.
Enjoy!!!
Monday, 3 September 2012
Cyber-crime laws in Malaysia
The use of computer and
the internet is on the increase due to lower costs of owning a computer and
connectivity and has become a mode of commercial and personal transactions and
an avenue for crimes to continue.
Cyber crimes are criminal offences
committed through the use of the computer and internet and this raise great
concern with the view to cyber fraud and identity theft through which crimes
such as spamming, phishing, email spoofing, defamation, pornography, cyber
terrorism, espionage and other rigid offences.
Cyber law refers to laws related to
governing and protecting the use of a computer and internet and other online
communication technologies, they focus on a combination of state and federal
statutory, decisional and administration laws arising out from the use of the
internet.
Since
information and communication technology in this era is becoming a vital issue,
Malaysia government has enacted cyber laws to govern and protect the user’s
right of the use of computer and internet.
We need cyber laws in place because
today so many issues have be brought on the platform regarding the integrity
and security of information, legal status of online transactions, privacy and
confidentiality of information, intellectual property rights and security
governing data input on the internet. Therefore such issues have led to the
enactment of cyber laws in Malaysia to help build confidence when dealing with
online activities whilst signifying why cyber laws are needed in online
transactions.
Since the internet has
no ownership and open to everyone, given the unrestricted number of free
websites, the internet is definitely unlocked for misuse. This means that users
of the internet have got to take security seriously by protecting customer’s
data, employee’s data and company data from internet fraud and identity theft.
Awareness is important; anything that seems
to be suspicious should be reported immediately until laws become more rigid or
when technology has advanced more.
Some challenges have been faced by the
authorities in tracking down perpetrators since they are very smart and use
secure software to stay anonymous. Therefore catching these criminals requires
high technology techniques. ( Chris Painter the Deputy chief of the Computer
Crime and Intellectual Property section of the U.S. Department of Justice), he
over sees a team of 22 lawyers involved in all aspects of computer crime, from
denial of service attacks to attacks on computer networks.
The Malaysian
government has so far tried to pass more than a few cyber laws to help reduce
and control the internet abuses such as reducing electronic transaction fraud
cases in Malaysia, which have built fear in individuals that use the computer
and the internet to confidently do business or transact online. And these cyber
laws that have been enacted and enforced from 1997 are as follows;
The Digital Act 1997 was enacted and
enforced to secure issues related to the way people electronically communicate
and transact business principally on the internet from abuses. Digital
signature is an identity verification that uses encryption techniques to
protect against email forgery, which help in protecting the transmitted data
from being interrupted or interfered with during electronic transactions. A
digital signature is obligatory when one obtains a Certificate Authority
licensed by the controller of authorities and any transaction held in
accordance to this Act and digitally signed is legally binding.
The Computer Crime Act, 1997
The Computer Crime Act, 1997
This Act was enacted to regulate computer
crimes and protect them against the misuse of computer criminal activities such
as hacking and cracking down of computer networks and systems and virus
spreading. This Law seems to be the most important due to increase in computer
activities such financial transactions, for example increase in electronic
banking. Through this Act, users of computers have been able to protect their
rights to privacy and confidence when using the computer. The Act is similar to
the United States Computer Fraud and Abuse Act 1986(United States), the
Computer Misuse Act 1990 (United Kingdome) and the Computer Misuse Act 1993
(Singapore). The offences covered under this Act are; Unauthorized access to
the computer without users permission, unauthorized modification, communication
of codes or passwords.
In
September 8, 2008 one of the offences under the Malaysia’s decade-age cybercrime
statute is going to be put on a test. At one proceeding in a session court in
Ipoh, a man has been charged with four counts relating to an illegal transfer
of land titles. The man is charged under section 5(1) of the Computer Crimes
Act 1997 that makes it an offence to modify contents of a computer or computer
system without authority. The accused claims trial and the case will be
mentioned on 9 Oct 2008. (http://bit.ly/QzjWFK).
The Act was enacted to regulate the practice
of medicine through the use of electronic data communication. The Telemedicine
Act guarantees that patient’s rights and interests are protected through
qualified medical practitioners who practice telemedicine with the consent of
patients. And these medical practitioners can be registered local Doctors who
have a valid operating certificate, Medical Assistant and Nurses approved by
Malaysian Medical of Health. The Act gives hope to the future growth and timely
delivery of healthcare in Malaysia.
Communication and Multimedia Act, 1998
Communication and Multimedia Act, 1998
This Act was enacted to promote the nations
policy objectives for the communication and multimedia sector in Malaysia and
ensure that the information is safe, reliable and the quality of services are
affordable for the public and instill the users confidence in the information
and communication technology sector. The Act legalizes various activities, for
example network service providers, application service providers and content
application providers after attainment of a license of operation. Eleven cases
have been taken to court under section 211 and 233 under this Act involving
fine to RM24,500 from last year up to now, cases like sending vulgar/obscene
SMS, sending obscene email and sending obscene/vulgar comments.
Case2:
KUALA
LUMPUR, July 6 (Bernama) -- A former EON Bank Berhad employee pleaded guilty in
the Sessions Court Monday over the posting of an obscene blog title to
embarrass his former boss. Seah
Boon Khim, 26, was accused of posting a vile and indecent material on a blog
site http://www.xanga.com/hokongchan67 with intent to annoy Eon Bank Internal
Audit Department head Ho Kong Chan at 1.33pm on Aug 13 2007 at 19 A-26-3 Level
6, UOA Centre 19, Jalan Pinang here (http://bit.ly/NYU6LY ). (Note, this case was published from local
national news agency called “Bernama”.
Bernama is owned by Malaysia government under the information, culture
and communication ministry.
Copy Right (Amendment) Act, 1997
Copy Right (Amendment) Act, 1997
The was enacted due to technological
development which have challenged governance of copy right issues in Malaysia,
such as to protect the right and control transmission of information over the
internet like music, books and films. In the subsequent years, this Act was
amended in 1990, 1996 and 1997, to give exclusive rights of control to the
Authors and set an abstract of offences for copy right infringement
Personal Data Protection Act, 2010
Personal Data Protection Act, 2010
The Act is intended to provide protection
of individual personal data in the perspective of commercial transactions and
safeguard the interests of data users, and all this boosts user’s confidence
and encourages electronic commerce. The Act sets rules and regulations on the
gathering and handling of personal information in companies and organizations
in the due course of any business transactions between the parties.
Case3:
A woman chief executive officer (CEO) filed a RM20mil
suit against a telecommunications company (telco) on Sunday for allegedly
revealing contents of her SMS exchanges and recordings of her teleconversations
with other individuals to third parties (http://bit.ly/oDzIN5).
Malaysia is trying to make every effort to
progress in a safe and confidential cyber space environment with the enactment
of several cyber laws which have helped to increase the computer and internet
usage in online transactions and due to the rapid development of technology,
requires reviewing and enactment of new cyber laws, as hackers are becoming
more equipped.
Thursday, 30 August 2012
How Easily Hacker Steal Your Personal Information
Today computers and humans can not be separated. Almost everyday human make interaction with computers (computer also includes: tablet PCs, smart phones, etc.) but not everyone is aware of the danger of cyber crime.
To raise the awareness of cyber crime in order to make people more aware and more be careful to do any activity and transactions that they do on the internet, below is short and interesting video about how hacker as a cyber criminal steal your data easily.
To protect yourself against hacker attack you can start from raising your concern on online data protection and security, then you can define the steps that need to be taken to prevent your self from hacker attack.
To raise the awareness of cyber crime in order to make people more aware and more be careful to do any activity and transactions that they do on the internet, below is short and interesting video about how hacker as a cyber criminal steal your data easily.
To protect yourself against hacker attack you can start from raising your concern on online data protection and security, then you can define the steps that need to be taken to prevent your self from hacker attack.
Wednesday, 29 August 2012
Online defamation in online security and privacy
Generally,
defamation is a false and unprivileged statement of fact that is harmful to
someone's reputation, and published "with fault," meaning as a result
of negligence or malice. Online defamation is the defamation or slandering of a business’s or
person’s reputation on the World Wide Web. Slandering in here is a defamatory statement expressed in a transitory
medium, such as verbal speech. It is considered a civil injury, as opposed to a
criminal offence.
Further concern of online defamation would
be cyberstalking, It has been defined as the use of information and
communications technology, particularly the Internet, by an individual or group
of individuals, to harass another individual, group of individuals, or
organization.
Computer misuse in online security and privacy

Computer misuse means the use of computers in the manner neither intended nor
authorized, and the use of a computer to facilitate
an offence.
The person who misuse the computer with able to offence
other computer for stealing password, privacy, and data from other computer
user is one of the biggest cyber crime. This kind of issue we steal have to
worry and aware from this kind of computer misuse. There are three points of
types of computer misuse that I want to explain, cause of these are three
points contain about online security and privacy thing:
Hacking
Hacking is an unconstitutional person uses a Internet
connection to get right of entry past security passwords or other security to
see data stored on another computer.
Data misuse and unauthorized transfer or copying
Copying and prohibited transfer of data is rapid and simple
by online computers and huge storage devices such as hard disks and memory
sticks. Company research and written work, such as books, cannot be copied not
including the exclusive rights holder's permission.
Identity and financial abuses
This topic includes misuse of stolen credit card numbers to
get goods or services on the Internet, and use of computers in financial
frauds.
With these three topics we should be careful of computer
misuse in this cyber era, if there is some issue that makes
you uncomfortable you may report it to cyber police which is now
available in every country.
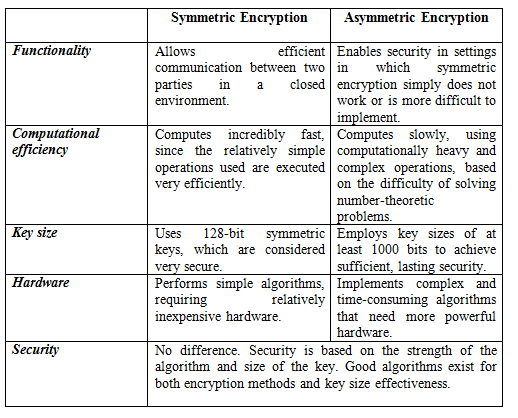
Symmetric encryption vs asymmetric encryption in multimedia communication
The principal aspects of the two encryption methods ( symmetric and Asymmetric key) are compared in the table below ( Reference Mohamed Abomhara, Khalifa, Othman Zakaria Omar, Zaidan A. A, Zaidan B. B. and Alanazi, Hamdan O. (2010), Journal of Applied Sciences))
Using symmetric key algorithms to secure online video streaming
Symmetric keys can provide
confidentiality but they cannot perform authentication, because there is no way
to prove through cryptography who had actually sent a message if two people are
using the same key. The following are the advantage and disadvantage of
using symmetric key systems to secure the online video streaming:
Advantages
- It is much faster than asymmetric key
systems.
- Its security is dependent on the length of
the key. With a large key size, the algorithm will be harder to break,
because symmetric algorithms carry out relatively simplistic mathematical
functions on the bits during the encryption and decryption processes.
- It does not require much computing power.
Disadvantages
- It requires a secure mechanism to deliver the
keys.
- Each pair of users needs a unique key; if
a user has N people to contact, then N secret keys must be maintained so
that as the number of individuals increases, so does the number of keys.
- Management of the symmetric keys can be problematic.
- Provides confidentiality but cannot authenticate, because the secret key is shared.
Tuesday, 21 August 2012
An Overview of the suitability of using symmetric key to secure multimedia data
With the increasing and continuous use of digital communications on the internet in recent times, security is becoming more and more relevant and important. However, special and reliable security is required for the many digital applications available such as video conferencing, digital television and mobile TV. The classical techniques of data security are not appropriate for the current multimedia usage. This study addresses the current algorithm of multimedia encryption schemes that have been proposed in the literature and description of multimedia security. It is a comparative study between symmetric key encryption and asymmetric key encryption in achieving an efficient, flexible and secure video data.( Mohamed Abomhara, Khalifa, Othman Zakaria Omar, Zaidan A. A, Zaidan B. B. and Alanazi, Hamdan O. (2010), Journal of Applied Sciences). ( http://irep.iium.edu.my/5618/).
A review on multimedia communications cryptography
Now-a-days, Due to the repaid increasing and continuous use of
multimedia communications on the internet, Security is becoming more and more
relevant and important. However, special and reliable security is required for
the many multimedia applications available such as video conferencing, digital
television and mobile TV. The classical techniques of data security are not
appropriate for the current multimedia usage. This study will presents the
currently algorithm of multimedia encryption schemes that have been proposed in
the literature and description the effectiveness of the multimedia security. It
is a comparative study between symmetric key encryption and asymmetric key
encryption in achieving an efficient, flexible and secure video data.
(Salem, Yasser, Mohamed Abomhara , Khalifa, Othman, Omer Zaidan, Aos Alaa Zaidan, and Bilal Bahaa (2011), Research Journal of Information Technology) ( http://irep.iium.edu.my/2241/).
(Salem, Yasser, Mohamed Abomhara , Khalifa, Othman, Omer Zaidan, Aos Alaa Zaidan, and Bilal Bahaa (2011), Research Journal of Information Technology) ( http://irep.iium.edu.my/2241/).
Subscribe to:
Comments (Atom)